Some people may sense the absence of authority over their personal data, especially in mobile apps. Nevertheless, the demand of mobile app developers/owners to have their hands on Personally Identifiable Information (PII) does not subside.
However, the risks should be taken into account, especially the regulations compliance. Adopting steps to safeguard user information is not just a legal requirement but also an ethical responsibility as data collection capabilities have a long-term effect on society.
So, this article is intended to show how developers can add data privacy options into their apps in an easy way to maintain the privacy of users.
Although the UI design and implementation techniques may change, this article will only focus on showing how data privacy functions are being implemented in simple database examples for React Native app development services.
Data design
This log is a tool for keeping a comprehensive history of user actions which could later assist in data procedures including those for individual users or specific user groups.
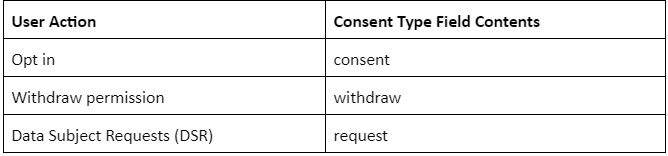
For each recorded action, three distinct fields were chosen:
The implementation was performed through a Cloudant NoSQL database mainly because of its affordable service tier for basic usage, but also because of the possibility of adding Android mobile libraries.
implementation group: "com.ibm.cloud", name: "cloudant", version: '0.0.32'
Enterprise data design
On the other hand, in order to ensure the highest level of protection, developers can select a Hyper Protect DBaaS solution either as a noSQL or SQL variant which provides workload isolation, restricted administrator access, and data in motion and at rest tamper protection.
To get the required Cloudant database, a simple CSV-import Python importer has been utilized, which also helps to create the indices from the samples record data elements. Subsequently, the following Java method was developed to post the JSON "document" containing the specified data fields of email, consent type, and date to the database:
public void saveUserPrivacy(String email, String consenttype) {
DocumentResult response;
Document registryDocument = new Document();
registryDocument.put("email", email);
registryDocument.put("consenttype", consenttype);
String currentDate = new SimpleDateFormat("yyyy-MM-dd:HH:mm:ss", Locale.getDefault()).format(new Date());
registryDocument.put("date", currentDate);
PostDocumentOptions documentOptions =
new PostDocumentOptions.Builder()
.db(getUserPrivacyDatabase())
.document(registryDocument)
.build();
if (isDoDebuglog())
Log.e(BlueListApplication.CLASS_NAME, "Adding " + registryDocument.toString());
try {
response = service.postDocument(documentOptions).execute().getResult();
} catch (Exception e) {
if (isDoDebuglog())
Log.e(BlueListApplication.CLASS_NAME, "Could not save user privacy preference. ", e);
}
}
Opt in
The option of unchecking the default must instead be presented in order to avoid accidentally bypassing the critical screening step. It is mandatory to use the option for users to do it consciously whether to opt in, and based on Play Store rules, privacy policies must be on the publicly accessible place.
Developers need to decide if such users' data should be neglected as personal information (PI) within their apps. For instance, if data collection and utilization of personal information are critical to the app's operation, the app may have to shut down. On the contrary, if the user grants PI, the app can apply a data obfuscation strategy to mask the user identification.
The mobile app requires the user to consent to logging in before they can access the system. The "Proceed" button is enabled only when the checkbox is checked, indicating the user's "Opt In" condition.
To implement the "Opt In" scenario, the "Consent Type Field Contents" mentioned earlier are utilized, requiring a straightforward method call:
saveUserPrivacy(email, "consent");.
Withdraw permission
Users have the right to revoke permissions they have previously consented to. Therefore, all PI data of that person should be deleted from the system, because it is processed data, which is collected, and even if not, it is processed.
"Controllers" determine the "whys" and "hows" of data processing operations, putting up rules users must understand and agree to before the app is used. This transparency enables users to make a choice of whether to go in or out depending on whether the data will be used currently or in the future.
"Processors" act on PI in accordance with the decision of the controller. If data is provided to a processor, he or she is expected to abide by the rules and actions set by the controller.
Developers must give users enough power to manage their data. Consequently, the "Data Controller" should provide a "Withdrawal Request" for withdrawing the consent for us and our "Data Processors" to handle user data.
Similar to the Consent feature, a withdrawal request can be logged with a simple call:
saveUserPrivacy(email, "withdraw")
Data Subject Request (DSR)
Users also have the right to ask for their personal data. As mobile developers, incorporating this functionality into mobile app security systems is very critical.
The UI for facilitating Data Subject Requests (DSR) is implemented in both an Android Settings Activity and an AlertDialog, offering choices to confirm the request.
Similar to the Consent and Withdrawal requests, a DSR can be logged with a straightforward call:
saveUserPrivacy(email, "request");
Conclusion
Data privacy rights can be readily implemented using basic database elements and a serverless monitoring agent. Developers can do the right thing and build trust with their user base, even when consumer protection legislation isn't always in place in some countries.
Innovative solutions targeted to your business needs are offered by Shiv Technolabs, a leader in React Native app development company. Utilize our knowledge to take your business presence to the next level and make the most of mobile technology.



No comments yet